
At a time when businesses are relying more than ever on technology, it's essential that all systems can work together seamlessly creating efficiencies and saving time. Unfortunately, this is often not the case. In a company there is often a whole set of software systems that standalone and people have the role of manually transferring data from one system to another to ensure that each system has the correct information to do its job. This manual synchronicity of the data between systems is costly and prone to error. Think of the negative consequences of a totally manual off-boarding process where a departing employee must be manually removed from all these various systems. How often do previous employees still have logon privileges to the network or an access card that still opens doors? Sadly, it is too often!
In this article, we explore the value of integrating, discuss the ideal way to integrate, and learn what Gallagher offers in this area.
Why integrate?
There is often a significant business value to linking several of the business systems together to exchange data or have some systems that share key parts of the data from a point of truth system. Connecting these systems, called integrating, can save staff a significant amount of time and ensure data integrity across the enterprise. We should not forget to consider the benefit of making the user experience of our people as good as it can possibly be.
Some would also promote the situation where you have the one super, unified, application that does everything as an alternative to integration. This will work for some, but others will want to choose the applications that perform specific functions to meet the needs of the company. Therefore, many companies will have several specialist applications that are integrated to meet their overall needs.
As an example, an enterprise may have HR, Visitor Management, Video Management, Analytics, and Active Directory Systems that work together to provide the security function required. Each of the systems will typically be the logical point of truth for some data items and other systems will consume those data items to associate with their own point of truth items.
When done properly the outcome is great data integrity that is easy for each system to consume. Employees are saving time by not performing mind numbing data replication; mistakes are minimized, and people can be adding value in more important activities.
So, what is the ideal mix?
There is no one-size-fits-all answer to this question and will depend on the specific needs of the business. When considering the choice of components for the security of a significant enterprise, chances are that the ERP and Network and Desktop application tools may be already established in the business, before looking at a new physical security system. A business may want to integrate these established tools into the selected security solution.
Video is an area where Gallagher have chosen to integrate to the best-in-class video systems and provide an API integration that gives the operators in Command Centre a consistent interface regardless of the video system being used.
Often a very large enterprise will desire the ability to analyse their activity data to look for efficiencies or anomalies in their physical access control system or, more powerfully, pull data from several of their systems to build a consolidated view across several of their business systems where there is the opportunity to glean more significant insights. To connect these tools together into a point of truth system, a business will need to consider integrating into an end-to-end security ecosystem.
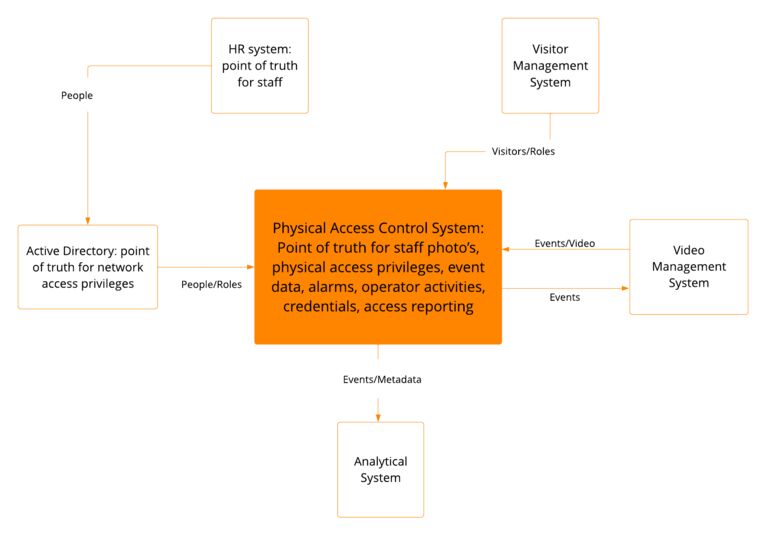
What is the best way of integrating these systems?
There are several tools and methods of integrating systems based on the tools the system is built with and the time that they have been developed.
For example, when Gallagher Command Centre was first released in the early 2000’s we created an interface for cardholder import and export based on Microsoft COM with XML data structures. We are now removing this integration technique mostly due to technology moving on such that it was quite technical and more challenging to secure.
We also have an integration tool called EDI (Enterprise Data Interface) which was envisioned to be an easy tool to use that would not require script or code to be written. EDI allows data from several different data sources to be viewed and for the administrator to choose to join various fields from the input source to the fields in Command Centres database. EDI allows batched data transfer mostly from a time-based trigger and fulfills the needs of many customers.
Over the past years we have been actively redeveloping our integration architecture to use REST. REST is accepted by most developers as the simplest and most reliable method of connecting to a server to transfer data.
Multiple data sets
Gallagher have partitioned the REST interface into several groups of functionality based around the types of transactions that the external system is wanting to achieve for example managing events and alarms and managing cardholders. Below are some examples of these groups:
- Alarms, events, and non-cardholder items
- Cardholders and related items
- Status and overrides
Alarms, Events, and non-cardholder items
The Events section will allow a client system to search for and fetch any event in the Gallagher Command Centre database.
Commonly this API allows another system to be able to display the events occurring in Command Centre where it may be merged into a superset of events from several different systems. The API allows the client application to receive events in real time which is often the intent if Command Centre is being connected to another monitoring centre.
Another use case is to feed the Gallagher events into an analytical engine that may also combine events from several sources. An enterprise might use this data to understand occupancy trends or even look for anomalies in staff member behavior.
The Event API also allows events generated by other systems to be sent to Command Centre to be merged with the events generated in Command Centre to allow the control room operators visualize the activity of an entire enterprise.
The Alarms section of the API allows an external system to behave as a peer of the Command Centre Alarm management subsystem.
Cardholders and related items
The Cardholder Rest API is used in many systems and is also an underlying API that is used by the Gallagher Active Directory integration. This API allows full management of people and their various Personal Data Fields (PDF’s), credentials (Access Cards or Mobile phone based), Access Group Membership where they receive their privileges to access various parts of a site, and Competencies. Competencies are an entity that represents anything that requires an approval of some sort and has an expiry date. A driver’s licence is an Example of a competency where the expiry date is used to remind the user, they need to renew the licence.
Status and overrides
The Status and Override API allows a client system to have a real time update of the status of some key items in Command Centre. The client system may use this live status to update the external system or for example it may turn on or off some status indicators or trigger an automation in the external system.
The API also allows the external system to trigger an override in Command Centre. An override is generally thought of as a temporary change to something and could be a request to unlock a door temporarily to let someone in or leave the door unlocked for a timed period, for example an hour. These overrides have the same ability that an operator at a Command Centre workstation, and of course any override that is actioned will be logged to the audit trail (events) listing the actioning operator, time, and the details of the override.
Security of integrating
The REST API’s can make significant changes to the system that affect site security, so it is vital that security of the machine-to-machine connection is very strong. The external system must possess an API key configured in Command Centre and uses certificates to authenticate that connection request is from the expected machine.
Sometimes the REST API client may be a machine on the internet and Gallagher have implemented a Cloud API Gateway that allows the client to connect to the Gallagher Cloud securely rather than requiring firewall changes to allow the incoming connection. This makes security much easier for the corporate Information Systems team, who prefer not to open ports on a firewall.
Licencing
Gallagher do require a licence to be purchased to use the various API’s to reflect the cost of developing and maintaining the API’s and the related security costs. Many Gallagher subsystems, for example the active directory integration or Command Centre Mobile, that use the REST API’s will not require those API licences as the related costs are included in the subsystem licence.
REST API’s provide developers with a powerful tool for integrating different systems. By using REST API’s, developers and operators can easily access data from a variety of sources and make it available in a central platform. This makes it possible to draw data from multiple sources and provide a united view of the data. This ensures systems are always up-to-date with the latest information. In short, REST API’s in Gallagher’s Command Centre offer a powerful way to integrate different systems and provide users with a streamlined experience. Integrated systems have the opportunity to save the enterprise cost and equally importantly improve the work experience of staff.